
Versace x Onitsuka Tiger will debut for SS26
Published September 30, 2025 Cool sneaker brands and designer labels are happily linking up at…











Overview Twonky Server version 8.5.2 is susceptible to two vulnerabilities that facilitate administrator authentication bypass on Linux and Windows. An unauthenticated attacker can improperly access a privileged web API endpoint to leak application logs, which contain encrypted administrator credentials (CVE-2025-13315). As a result of the use of hardcoded encryption keys, the attacker can then decrypt…

Outsmart attackers with smarter rules Managing network security in a dynamic cloud environment is a constant challenge. As traffic volume grows and threat actors evolve their tactics, organizations need protection that can scale effortlessly while delivering robust, intelligent defense. That’s where a service like AWS Network Firewall becomes essential, and we’re excited to partner with…

Every great product experience starts with a smooth beginning. But in the world of cloud security, onboarding can sometimes feel like an obstacle course. Detailed fine-grained Identity and Access Management (IAM) configurations, lengthy deployment steps, and manual permission setups can turn what should be an exciting first impression into a tedious chore. That’s changing. Rapid7…

CVE-2025-64446 – Fortinet’s FortiWeb exploitation A critical vulnerability in Fortinet’s FortiWeb Web Application Firewall, now assigned CVE-2025-64446 (CVSS 9.1), allows unauthenticated attackers to gain full administrator access to the FortiWeb Manager interface and its websocket CLI. The flaw became publicly known on October 6, 2025, after Defused shared a proof-of-concept exploit captured by their honeypots….

Ransomware has evolved from simple digital extortion into a structured, profit-driven criminal enterprise. Over time, it has led to the development of a complex ecosystem where stolen data is not only leveraged for ransom, but also sold to the highest bidder. This trend first gained traction in 2020 when the Pinchy Spider group, better known…

Shannen HeadleyWest Midlands BBC The school will be shut on Wednesday and Thursday, said a letter to staff and parents A secondary school in Cheshire has been shut to deep clean the building after high levels of pupil sickness. Congleton High School told parents and staff it contacted the UK Health Security Agency and infection…

Juliette Parkin,in Brightonand Hsin-Yi Lo,South East Family handout Ellame Ford-Dunn was found dead in the grounds of Worthing Hospital in March 2022 An NHS trust has been fined £200,000 for failing to provide “safe care and treatment” for a 16-year-old girl who died on hospital grounds after fleeing her ward. Ellame Ford-Dunn, from Upper Beeding,…

A series of events are to be held at Wolverhampton’s libraries in a bid to bring communities together during the colder months. The Winter Warmth and Wellness sessions will take place at venues across the city between 4 December and 27 January. Councillor Bhupinder Ghakal, of City of Wolverhampton Council, said they would give people…

Modern AI applications demand fast, cost-effective responses from large language models, especially when handling long documents or extended conversations. However, LLM inference can become prohibitively slow and expensive as context length increases, with latency growing exponentially and costs mounting with each interaction. LLM inference requires recalculating attention mechanisms for the previous tokens when generating each…
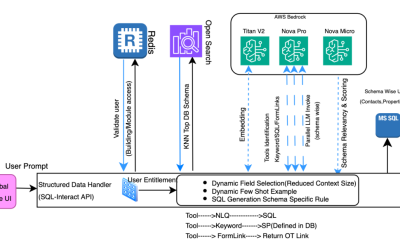
This post was written with Lokesha Thimmegowda, Muppirala Venkata Krishna Kumar, and Maraka Vishwadev of CBRE. CBRE is the world’s largest commercial real estate services and investment firm. The company serves clients in more than 100 countries and offers services ranging from capital markets and leasing advisory to investment management, project management and facilities management….